FAQs
ONYEN
- Make sure your e-mail program knows and stores the new password, then close your e-mail program.
- Make sure your iPhone, iPad, Android, or anything else that you use to check your e-mail has been updated.
- If you’re running Windows, sign out and back in to update the stored copy that Windows keeps.
- If you suspect that your account has been locked, call us at 919-962-4800 to have it unlocked.
- The campus help desk is also available for 24/7/365 support at 962-HELP.
- Usually, the first three steps above will clear up any password problems.
IT Security
Please review this article for help on identifying a phishing email (scroll down).
Key highlights from the above article:
How to spot phishing
Many phishing emails follow similar patterns. Here are a few things to watch out for:
- The “from” address doesn’t match the sender name or is an attempt to look like someone affiliated with the University, like Chancellor.unc.edu@gmail.com.
- The “to” field includes a bunch of other people, or it’s blank and you are blind carbon copied (bcc’ed).
- The email has poor spelling and grammar. It may also feel stilted or like it’s written by AI.
- There’s a sense of urgency or emotional manipulation. Common ploys are you must act now or bad things will happen or that you’ll miss out on an opportunity if you wait.
Anatomy of a phishing email: View Infographic
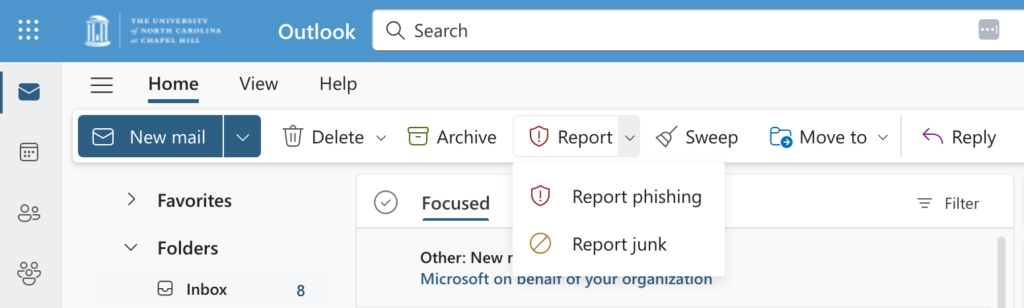
For Outlook online (Heelmail) and desktop Outlook on Windows and Mac, first select the phishing email, then click the Report button in your toolbar. You can find the toolbar directly above your inbox — it includes commonly used actions like deleting or marking items as read.
According to University policy, sensitive information is defined as Tier 2 and Tier 3 information as outlined here: Information Classification Standard
Some Tier 2 and 3 information is in defined categories because it is covered by a specific law, regulation, or industry standard. These include:
- Personally Identifying Information, as defined by the North Carolina Identity Theft Protection Act of 2005
- Protected Health Information, as defined by the Health Insurance Portability and Accountability Act of 1996 (HIPAA)
- Student education records, as defined by the Family Educational Rights and Privacy Act (FERPA)
- Customer record information, as defined by the Gramm Leach Bliley Act (GLBA)
- Confidential personnel information, as defined by the State Personnel Act
- Information that is deemed to be confidential in accordance with the North Carolina Public Records Act
If you have access to sensitive information because of your role with the University, you share a responsibility to protect that information. If you are unsure whether information you have is “sensitive” there are people responsible for Data Governance who can help. The Data Governance Oversight Group can provide guidance. Information on University Data Governance is available at Data Governance at UNC.
If you believe that University sensitive information may be compromised, call 919-962-HELP and request a critical ticket for an Information Security Analyst.
If you have questions about how to appropriately secure information, please consult Hussman IT by submitting a ticket via help.unc.edu. Information is available on the University SafeComputing web site to help with specific topics. The University’s Privacy Office is a good resource for information on many types of sensitive information.
In general, sensitive information may be stored in the Office 365 environment (e.g., OneDrive) provided by the University. If you have storage needs beyond the Office 365 environment please consult Hussman IT.
Equipment Room
Printing / Classrooms / Building Access
- Hussman-owned computers may print directly to any Xerox Multi-function Device (MFD).
- Windows users may install the printer queues via the Software Center app.
- Mac users may install the printers via the Self Service app.
- You may retrieve your print job from any Xerox MFD in Carroll Hall.
- Faculty/staff/instructors may print from personal computers via Mobile Print.
- For students, there are CCI printers available throughout campus. Visit CCI Printing for more information.
Access: Data and Services On/Off Campus
File Server Access Requests
If you’re still having trouble after going through those steps, you’ll want to contact 962-HELP directly (or submit a ticket).
We can attempt to help you if you are in Carroll Hall, but Hussman IT won’t be able to resolve any issues that may exist with the service since this is a central ITS supported service. We can only act as a support liaison for you.
The Duo app works by prompting you to confirm your login, whenever you try to access a service that it is configured to secure. The process looks something like this…
* Attempt to log on to a service configured to be secure by Duo, such as the UNC VPN
* You will log on in the usual way, using your ONYEN credentials
* Once you submit your credentials, Duo is triggered
* If you have the app setup on your smartphone, you’ll receive a push notification to confirm that it is you
* If configured for a landline or cell number, you’ll receive an automated phone call
* Once confirmed, you’ll be able to immediately log in
The ITS helpdesk is available to answer any questions with this service and at your disposal (24/7) if you ever run into an access issue. They can be reached at 962-HELP or help.unc.edu.
Applications
Sakai will be replaced by Canvas after Spring 2024.
If it has not been reported, forward your email as an attachment to phish@unc.edu so it can be reviewed and blocked by security. Make sure you’re forwarding the email as an attachment!